Digital Signatures
May 31, 2012 Leave a comment
Every day, we sign our names to letters, credit card receipts, and other documents, demonstrating they are in agreement with the contents. That is, we authenticate that they are in fact the sender or originator of the item.
Written signatures are also vulnerable to forgery because it is possible to reproduce a signature on other documents as well as to alter documents after they have been signed.
Digital signatures enable the recipient of information to verify that the information is intact.
A digital signature serves the same purpose as a handwritten signature. It is really tough to counterfeit the contents of the information.
Digital signatures and hand-written signatures both rely on the fact that it is very hard to find two people with the same signature. Public Key Cryptography is used to compute the digital signatures.
Hashes
A one-way hash function takes variable length input, which can be the size of any length and produces a fixed length message. The hash function ensures that, if the information is changed in any way, even just one bit, a different output value is produced. You can’t recreate the original text.
For example, consider simple text – “Welcome to the Zero Production Incidents Blog”. A Simple example of hash creation can be multiplying the number of letters by number of words. 39 letters and 7 words. Our hash value is 39X7=273.
While transferring, if the string value is changed, it will impact the hash value. Since it is a simple hash calculation method, there are chances that the same hash value can be obtained by changing the string.
With Complex hash algorithms, that are actually used, it would be impossible to get the same hash value for a different text.
Message digests
Message digests are fixed size numeric representations of the contents of messages, which are inherently variable in size.
A message digest is computed by a hash function, which is a transformation that meets two criteria:
- The hash function must be one-way. It must not be possible to reverse the function to find the message corresponding to a given message digest, other than by testing all possible messages.
- It must be computationally infeasible to find two messages that hash to the same digest.
A message digest is also known as a Message Authentication Code (MAC), because it can provide assurance that the message has not been modified. A message-digest algorithm is also called a one-way hash algorithm or a hash algorithm.
Message-Digest Algorithms properties required to be cryptographically secure
- It must not be feasible to determine the input message based on its digest
- It must not be possible to find an arbitrary message that has a particular, desired digest
- It should be impossible to find two messages that have the same digest (collision)
- It should be very sensitive to input message changes
Digital timestamps may be used in connection with digital signatures to bind a document to a particular time of origin.
Digital Signatures
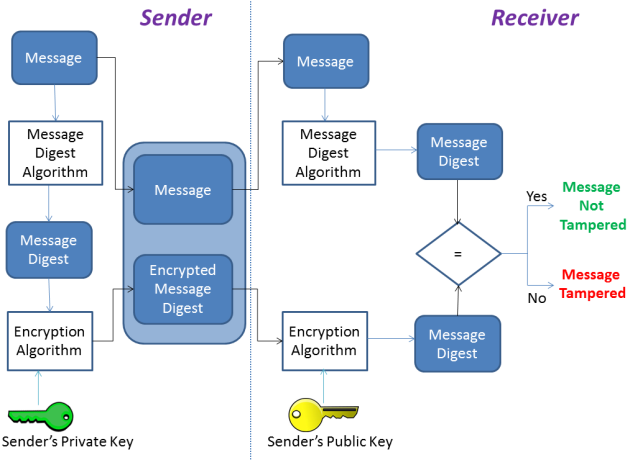
A digital signature is a piece of data which is attached to a message and which can be used to find out if the message was tampered with during the conversation. A digital signature is formed by encrypting a representation of a message. The basic manner in which digital signatures are created is illustrated in the figure below.
The following steps are performed at the Sender:
- Create the Message Digest using the Message Digest Algorithm.
- Encrypt the Message Digest with the Private Key using the Encryption Algorithm.
- Plain text along with Message Digest is sent to the Sender.
Once the Message is received, the following steps are performed at the Receiver
- Decrypt the Message Digest present in the Message, using the Sender’s public key .
- Uses the same message digest algorithm used by the sender to generate a message digest of the received message.
-
Compares both message digests (the one sent by the sender as a digital signature, and the one generated by the receiver). If they are not exactly the same, the message has been tampered with by a third party.
Using public-key cryptography in this manner ensures integrity, because we have a way of knowing if the message we received is exactly what was sent by the sender. However, the above example guarantees only integrity. The message itself is sent unencrypted. This is not necessarily a bad thing: in some cases we might not be interested in keeping the data private, we simply want to make sure it isn’t tampered with.
The encryption uses the private key of the signatory and, for efficiency, usually operates on a message digest rather than the message itself.
If the digital signature is verified, the receiver knows that:
- The message has not been modified during transmission.
- The message was sent by the entity that claims to have sent it.
Digital signatures are part of integrity and authentication services. Digital signatures also provide proof of origin. Only the sender knows the private key, which provides strong evidence that the sender is the originator of the message.
Note: We can also encrypt the message itself, which protects the confidentiality of the information in the message.
A digital signature functions for electronic documents like a handwritten signature does for printed documents. The signature is an unforgeable piece of data that asserts that a named person wrote or otherwise agreed to the document to which the signature is attached.